GootLoader was born from GootKit, a banking trojan that first appeared around 2014. In recent years GootKit has evolved into a sophisticated and evasive loader — and it was given a new name to reflect its new purpose in 2021. The same group is responsible for both versions of the malware, and is monitored by Mandiant as UNC2565.
The evolution of GootLoader reflects the evolution of cybercriminal gangs. Many of the more sophisticated gangs are switching to a malware-as-a-service business model. They develop the malware, but less-advanced gangs or individuals pay for use of that malware. In this case, it is access (or victim) as a service. GootLoader provides access to victims primarily for ransomware. The access is likely taken up by ransomware-as-a-service (RaaS) groups who sell-on the access to ransomware groups or individual criminals. For further details on this business model, see Cyber Insights 2023: Criminal Gangs.
GootLoader continues to evolve. Researchers at Cybereason have published a deep dive into the latest version.
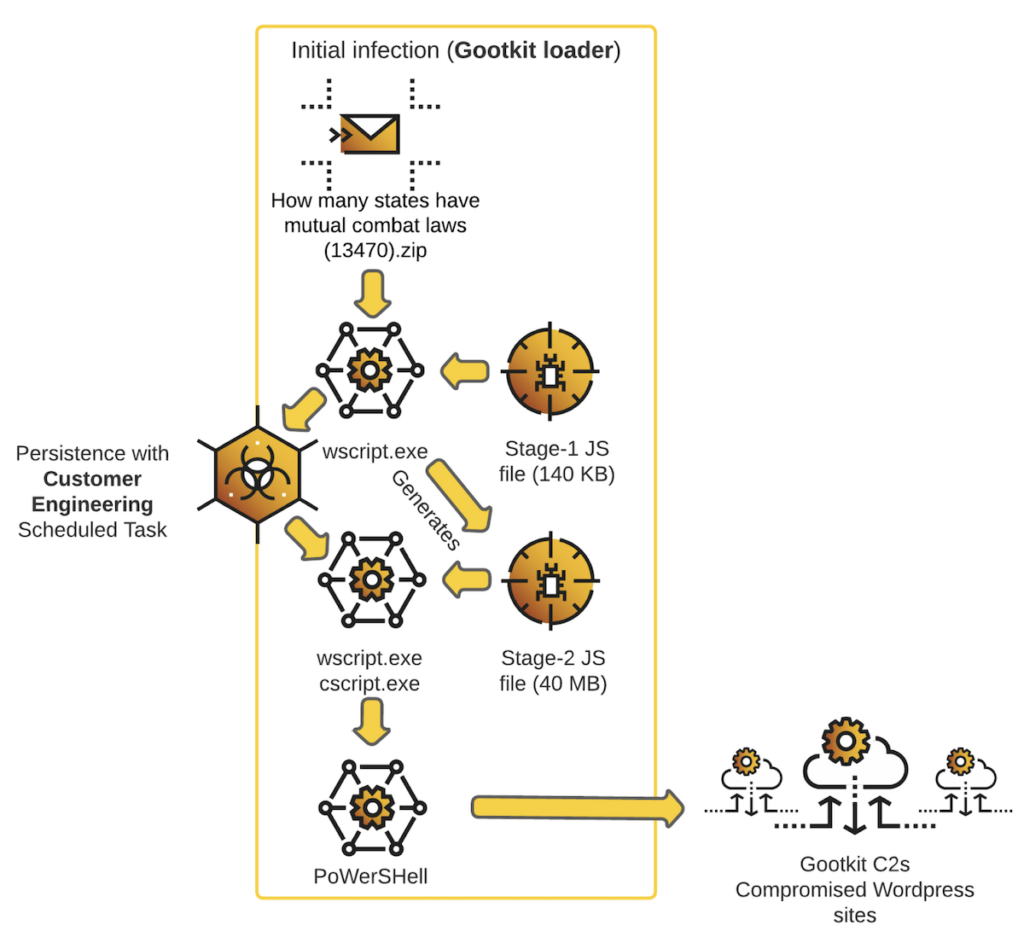
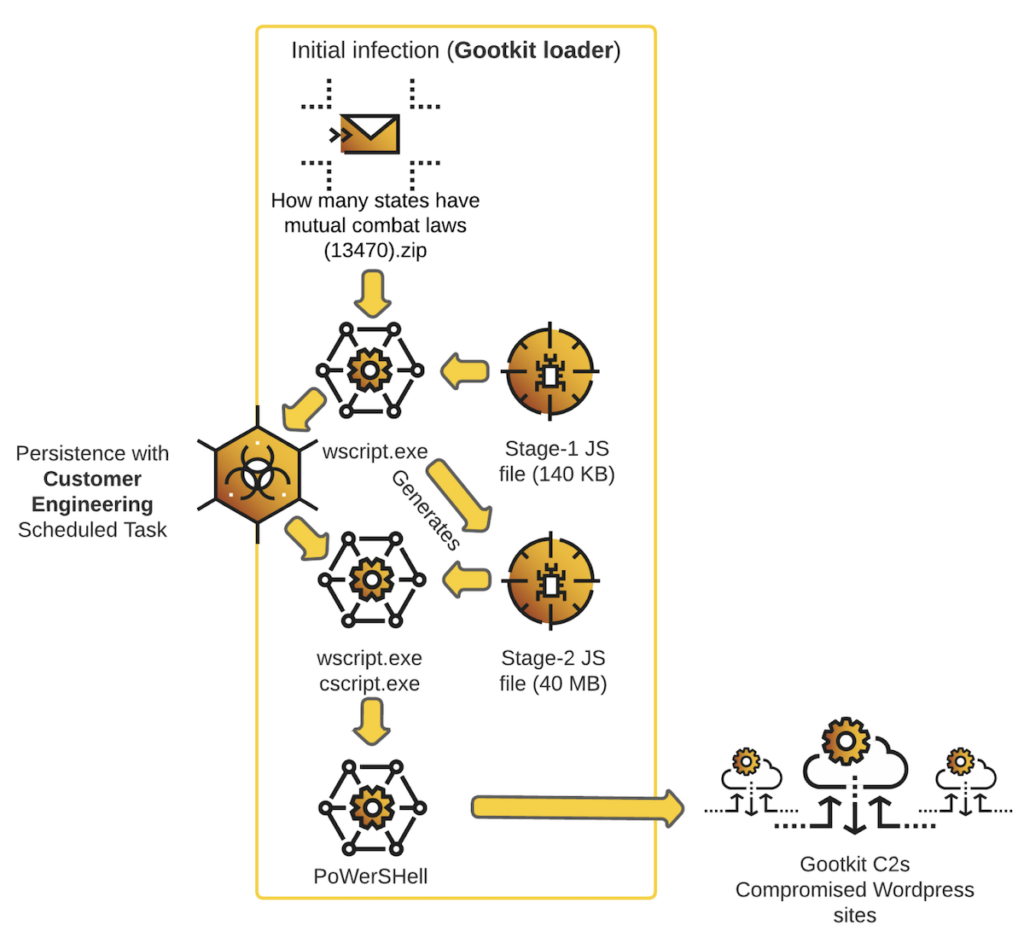
The infection journey starts within compromised WordPress sites. These sites are given greater validity through SEO poisoning techniques, with key words likely hidden within html code on valid pages. Google Ads may also be used. With a high search engine ranking, potential victims are more likely to visit the compromised site.
The primary targets are healthcare and finance within English speaking countries, such as the US, the UK and Australia.
If a victim is drawn into a watering hole WordPress site, he is provided with a ZIP file containing a malicious JavaScript. This is described as stage-1 of the GootLoader infection. The JavaScript establishes persistence by creating and running a ‘Customer Engineering’ scheduled task. It also generates a second JavaScript file (stage-2 of the infection) which is 40 MB in size (random junk code is added, probably to confuse and evade detection).
The Customer Engineering task has been configured to execute this large new JavaScript file. It ultimately provides PowerShell code, which executes a command and control function every 20 seconds using random GootLoader C2 URLs as parameters. It uses system discovery calls to obtain the environment variables, processes, desktop items and disks on the victim machine. This data is compressed, and encoded, and sent to the C2 disguised as a cookie.
As an aside, the researchers used ChatGPT to make some of the PowerShell code more easily understood. It was used, for example, to change the original variable names into more descriptively pertinent names. This it did effectively, but researcher Loic Castel told SecurityWeek that ChatGPT’s value to seasoned researchers is limited. “It cannot help with the more complex work – couldn’t help with the de-obfuscation – but it may be used by junior researchers in more basic stages.”
Lateral movement starts with disabling Microsoft Defender, and proceeds with Cobalt Strike loaded through DLL hijacking. SystemBC is deployed.
Cybereason was unable to see the final effect of GootLoader. The instance comes from its own telemetry where it detected and stopped GootLoader’s progress. The final malware deployment didn’t happen. But they did detect the deployment of SystemBC.
“SystemBC is what we call the precursor of ransomware,” explained Castel. “We often see it hours, maybe days, before the ransomware is actually deployed. This is something that is often deployed just before a ransomware attack.”
Any subsequent ransomware attack would almost certainly not have been delivered by UNC2565. Their function within the modern criminal ecosphere is to provide access to victims, and to sell that access to other criminals. The final payload is not pre-defined, but it seems likely to be particularly relevant for ransomware.
GootLoader is not a specifically targeted attack. However, some generalized targeting is achieved through the development of the original watering hole process. This suggests that this instance of the malware is aimed at the healthcare and finance sectors within English-speaking countries.
Cybereason assesses the GootLoader threat level as ‘severe’. The malware uses a combination of evasion and living off the land techniques, and its presence is unlikely to be spotted by anything other than AI-assisted anomaly detection.
Related: Ransomware, Malware-as-a-Service Dominate Threat Landscape
Related: Recent GootLoader Campaign Targets Law, Accounting Firms
Related: Mouseover Macro Campaign Delivers Gootkit Trojan Via PowerPoint
Related: GootKit Trojan Targets Banks With Redirection Attacks
The post A Deep Dive Into the Growing GootLoader Threat appeared first on SecurityWeek.