A vulnerability affecting IBM’s Aspera Faspex file transfer solution, tracked as CVE-2022-47986, has been exploited in attacks.
The post Recently Patched IBM Aspera Faspex Vulnerability Exploited in the Wild appeared first on SecurityWeek.
A vulnerability affecting IBM’s Aspera Faspex file transfer solution, tracked as CVE-2022-47986, has been exploited in attacks.
The post Recently Patched IBM Aspera Faspex Vulnerability Exploited in the Wild appeared first on SecurityWeek.
Organizations worldwide have been warned of an increase in the number of attacks abusing Microsoft OneNote documents for malware delivery.
Part of the Office suite, OneNote is typically used within organizations for note taking and task management, among other operations.
What makes OneNote documents an attractive target for threat actors includes the fact that they do not benefit from the Mark-of-the-Web (MOTW) protection, along with the fact that files can be attached to OneNote notebooks and then executed with minimal warnings.
In August last year, security researchers warned that MOTW was not applied to OneNote attachments, meaning that unsigned executables or macro-enabled documents could be used to bypass existing protections.
According to WithSecure, however, Microsoft last month silently patched the ability to bypass MOTW for OneNote attachments, which decreases the potential for abuse, but does not completely eliminate it, allowing threat actors to embed files in OneNote documents and lure users into executing them.
Attacks abusing OneNote documents for malware delivery are not different from those using other types of malicious Office files: under different pretenses, the user is tricked into opening the document and enabling editing, which results in the execution of attached code.
In December 2022 and January 2023, Proofpoint observed more than 50 malicious campaigns abusing OneNote documents for the delivery of malware such as AsyncRAT, AgentTesla, DoubleBack, NetWire RAT, Redline, Quasar RAT, and XWorm.
Both Proofpoint and Sophos observed initial access broker TA577 joining the fray at the end of January, relying on the same technique for the delivery of Qbot (also known as Quakbot).
The observed campaigns are different in volume, some targeting a small number of industries, while others involve thousands of messages sent to numerous recipients. According to Proofpoint, the attacks targeted organizations worldwide, with a focus on North America and Europe.
“Based on data in open-source malware repositories, initially observed attachments were not detected as malicious by multiple antivirus engines, thus it is likely initial campaigns had a high efficacy rate if the email was not blocked,” Proofpoint notes.
According to Opalsec, the list of malware delivered via malicious OneNote documents also includes the Formbook infostealer, the IcedID trojan, and the Remcos RAT.
Security researcher Marco Ramilli says that the abuse of OneNote for malware delivery has been ongoing for more than four months. The observed payloads, he says, include some of the aforementioned remote access trojan (RAT) families.
These attacks are efficient because the target interacts with the malicious document. Thus, educating users and employees on not opening files received from untrusted sources can mitigate risks.
Related: Malicious Macro-Enabled Docs Delivered via Container Files to Bypass Microsoft Protections
Related: Microsoft Resumes Rollout of Macro Blocking Feature
Related: Microsoft Restricts Excel 4.0 Macros by Default
The post Microsoft OneNote Abuse for Malware Delivery Surges appeared first on SecurityWeek.
A newly identified threat actor has been targeting military organizations in Pakistan with sophisticated malware, BlackBerry reports.
Tracked as NewsPenguin, the adversary has been observed sending phishing emails that use the upcoming Pakistan International Maritime Expo & Conference (PIMEC-2023) as bait and which carry weaponized documents to deliver an advanced espionage tool.
Running February 10-12, PIMEC is an initiative of the Pakistani Navy that helps private and public organizations showcase products and develop relationships.
NewsPenguin’s malicious documents, which pose as an exhibitor manual that appears to target PIMEC visitors, carry embedded Visual Basic for Applications (VBA) macros to execute malware.
Once opened, the lure document uses a remote template injection technique to fetch the next stage from a remote server that only serves the payload to Pakistani IP addresses.
The victim is prompted to enable editing in the document and, once that happens, embedded VBA macro code is executed to save an RTF file on the machine. The script also checks the OS version, invokes the command prompt, and adds a registry key for persistence.
Multiple other files leading to the final payload are also downloaded on the victim’s machine. NewsPenguin’s agent, which is injected into explorer.exe, is a previously undocumented espionage tool that can bypass sandboxes and virtual machines (VMs).
NewsPenguin performs multiple checks to determine whether it runs in a sandbox environment, then connects to a hardcoded remote server to receive the IP of the command-and-control (C&C) server and start receiving commands, which are base64 encoded.
The researchers discovered that the malware waits five minutes between commands, likely another attempt to bypass sandboxes, which typically have a time limit of fewer than five minutes per sample.
Based on received commands, the malware collects and sends information about the machine, runs an additional thread, copies or moves files, deletes files, creates directories, sends the content of files to the server, executes files, and uploads or downloads files from the server.
Domains associated with these attacks were registered in the second half of 2022, showing that NewsPenguin has been planning the operation for a while.
The threat actor’s targets include military technology companies, nation-states, and military organizations in Pakistan, including PIMEC organizers, exhibitors, and visitors.
“Given the highly focused nature of the targets (the Pakistan maritime industry), previously unseen tooling, and new network infrastructure, it is unlikely that the threat actor behind it is connected to casual cybercrime. Instead, we consider it highly likely that the attacker is a nation-state or an outsourced team working for a nation-state threat actor,” BlackBerry concludes.
Related: Nation-State Hacker Attacks on Critical Infrastructure Soar: Microsoft
Related: After Nation-State Hackers, Cybercriminals Also Add Sliver Pentest Tool to Arsenal
Related: Sophisticated Cyberattack Targets Pakistani Military
The post Military Organizations in Pakistan Targeted With Sophisticated Espionage Tool appeared first on SecurityWeek.
The US Treasury on Thursday slapped sanctions against seven Russians accused of running the notorious Trickbot cybercrime operation, freezing assets in multiple countries and imposing travel bans.
The seven individuals are being blamed for a series of major ransomware attacks targeting organizations in the US and the United Kingdom and the Treasury Department said it has information linking the hacking group to Russian intelligence services.
“Current members of the Trickbot Group are associated with Russian Intelligence Services. The Trickbot Group’s preparations in 2020 aligned them to Russian state objectives and targeting previously conducted by Russian Intelligence Services. This included targeting the U.S. government and U.S. companies,” the department said in a statement announcing the cross-border sanctions.
The sanctioned Russians include:
The notorious Trickbot cybercrime operation was born out of a malware first identified in 2016 that conducted online bank robberies out of Moscow, Russia. The US estimates that the Trickbot malware infected millions of victim computers worldwide, including those of U.S. businesses, and individual victims.
The malware has since evolved into a highly modular malware suite run by a Trickbot Group that regularly launches data-encryption and extortion (ransomware) attacks.
Trickbot has been known to target hospitals and healthcare centers across the United States with ransomware attacks that disrupt computer networks and telephones, sometimes causing a diversion of ambulances and medical resources.
“Members of the Trickbot Group publicly gloated over the ease of targeting the medical facilities and the speed with which the ransoms were paid to the group,” the Treasury said.
As a result of the sanctions, assets in the US and the UK will be frozen and travel bans will be imposed. In addition, the government warns that making funds available to the individuals (via ransom payments, including in crypto assets) is prohibited under these sanctions.
Related: IBM Dives Into TrickBot Gang’s Malware Crypting Operation
Related: Conti Ransomware ‘Acquires’ TrickBot as It Thrives Amid Crackdowns
Related: Russian Man Extradited to U.S. for Role in TrickBot Malware Development
Related: TrickBot Botnet Survives Takedown Attempt
The post US, UK Slap Sanctions on Trickbot Cybercrime Gang appeared first on SecurityWeek.
A recently identified financially motivated threat actor is targeting companies in the United States and Germany with custom malware, including a screenlogger it uses for reconnaissance, Proofpoint reports.
Tracked as TA866, the adversary appears to have started the infection campaign in October 2022, with the activity continuing into January 2023.
As part of the campaign, which Proofpoint refers to as Screentime, victims are targeted with malicious emails containing an attachment or a URL that leads to the deployment of malware. In some cases, based on the attacker’s assessment of the victim, post-exploitation activity may commence.
In October and November 2022, a small number of companies in the US were targeted with emails carrying Publisher file attachments containing malicious macros.
In November and December, the attackers switched to using URLs leading the intended victims to Publisher files containing macros or to JavaScript files. Some of the emails were seen carrying PDF attachments containing URLs to JavaScript files.
After switching to URLs, the attackers also scaled the campaign, sending thousands or tens of thousands of malicious messages several times per week, targeting thousands of organizations. In January 2023, the email volume increased even more, but the frequency of attacks was reduced, Proofpoint says.
Emails observed in January appeared to use thread hijacking with a ‘check my presentation’ lure to trick recipients into clicking the malicious URLs.
The malicious links lead to the 404 TDS (traffic distribution system) that filters the traffic and redirects the victim to a JavaScript file. If the victim runs the file, a MSI package is fetched and executed, which in turn runs an embedded VBS script and achieves persistence.
The script is the WasabiSeed malware, which downloads and executes another MSI file representing a piece of malware named Screenshotter, and then continues polling the URL for additional payloads.
With variants implemented in different programming languages (including Python, AutoIT, and JavaScript/IrfanView), Screenshotter was designed to take screenshots of the victim’s screen and send them to a command-and-control (C&C) server.
According to Proofpoint, the attackers likely manually inspect the screenshots and use WasabiSeed to deploy additional payloads if the victim is deemed interesting, such as the AHK Bot, which too enters a loop to fetch additional components.
AHK Bot has been observed deploying a script to check the victim machine’s Active Directory (AD) domain and downloading and loading in memory the Rhadamanthys information stealer. The AD profiling, Proofpoint notes, could lead to the compromise of other domain-joined hosts.
Proofpoint has been tracking the use of 404 TDS since September and believes that it is either sold or shared between cybercriminals, as it has been used in various phishing and malware campaigns.
As part of TA866’s Screentime campaign, hundreds of random URLs were used, leading to 20 domains that were registered on the day of the attack.
“These domains were previously registered, expired, and then re-sold to the TDS operator,” Proofpoint notes.
Some parts of the observed attacks involve manual interaction from the threat actor and, based on payload download time, Proofpoint’s security researchers believe that TA866 could be residing in the UTC+2 or UCT+3 time zones. These time zones correspond, among others, to Russia.
Furthermore, the researchers discovered that AHK Bot contains Russian language variable names and comments, and that the malware has been used in attacks since at least 2019, with some of the previous activity seemingly having an espionage objective.
“TA866 is a newly identified threat actor that distributes malware via email utilizing both commodity and custom tools. Most of the activity recently observed by Proofpoint suggests recent campaigns are financially motivated, however assessment of historic related activities suggests a possible, additional espionage objective,” Proofpoint concludes.
Related: North Korean Hackers Created 70 Fake Bank, Venture Capital Firm Domains
Related: Vietnam-Based Ducktail Cybercrime Operation Evolving, Expanding
Related: US Government Agencies Warn of Malicious Use of Remote Management Software
The post Cybercrime Gang Uses Screenlogger to Identify High-Value Targets in US, Germany appeared first on SecurityWeek.
There have been some new developments in the case of the ESXiArgs ransomware attacks, including related to the encryption method used by the malware, victims, and the vulnerability exploited by the hackers.
After the US Cybersecurity and Infrastructure Security Agency (CISA) announced the availability of an open source tool designed to help some victims of the ESXiArgs ransomware recover their files without paying a ransom, the FBI and CISA released a document providing recovery guidance.
The FBI and CISA are aware of more than 3,800 servers that were compromised around the world in ESXiArgs ransomware attacks.
Currently, the Shodan and Censys search engines show 1,600-1,800 hacked servers, but there is indication that many impacted organizations have started responding to the attack and cleaning up their systems.
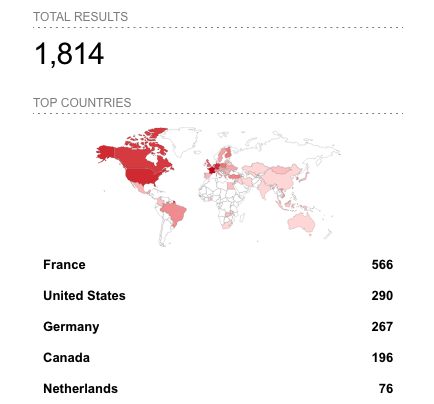
Reuters has conducted an analysis and determined that the victims include Florida’s Supreme Court and universities in the United States and Europe.
An analysis of the file-encrypting malware deployed in the ESXiArgs attacks showed that it has targeted files associated with virtual machines (VMs). However, experts noticed that the ransomware mainly targeted VM configuration files, but did not encrypt the flat files that store data, allowing some users to recover their data.
The tool released by the US government reconstructs the encrypted configuration files based on the unencrypted flat files.
However, Bleeping Computer reported on Wednesday that some victims have been targeted with a new version of the ESXiArgs malware, one with a different encryption process that involves encrypting more data, which prevents the recovery of files.
Until now, the ransomware did not encrypt the majority of data in large files, but the new version of the malware encrypts a far more significant amount of data in large files. Up until now, researchers have not found any flaws in the actual encryption, making it impossible to restore encrypted files.
It has been assumed that the ESXiArgs attacks leverage CVE-2021-21974 for initial access. This is a high-severity remote code execution vulnerability in VMware ESXi that VMware patched in February 2021. The issue is related to OpenSLP.
VMware has not confirmed exploitation of CVE-2021-21974, but it did say that there is no evidence of a zero-day vulnerability being leveraged in the attacks.
However, threat intelligence company GreyNoise is not convinced that there is enough evidence that CVE-2021-21974 is being exploited. GreyNoise pointed out that several OpenSLP-related vulnerabilities have been found in ESXi in recent years, and any of them could have been exploited in the ESXiArgs attacks, including CVE-2020-3992 and CVE-2019-5544.
Data collected by cloud security company Wiz showed that, as of February 7, 12% of ESXi servers were unpatched against CVE-2021-21974 and vulnerable to attacks.
The attacks have yet to be attributed to a known threat actor, but the evidence collected so far suggests that the file-encrypting malware is based on Babuk source code that was leaked in 2021.
“Due to the relatively low ransom demand (2 BTC) and widespread, opportunistic targeting, we assess with moderate confidence this campaign is not tied to ransomware groups known for ‘Big Game Hunting’,” said SOC-as-a-service provider Arctic Wolf. “More established ransomware groups typically conduct OSINT on potential victims before conducting an intrusion and set the ransom payment based on perceived value.”
Related: VMware Patches VM Escape Flaw Exploited at Geekpwn Event
Related: VMware Confirms Exploit Code Released for Critical vRealize Logging Vulnerabilities
The post ESXiArgs Ransomware Hits Over 3,800 Servers as Hackers Continue Improving Malware appeared first on SecurityWeek.
GootLoader was born from GootKit, a banking trojan that first appeared around 2014. In recent years GootKit has evolved into a sophisticated and evasive loader — and it was given a new name to reflect its new purpose in 2021. The same group is responsible for both versions of the malware, and is monitored by Mandiant as UNC2565.
The evolution of GootLoader reflects the evolution of cybercriminal gangs. Many of the more sophisticated gangs are switching to a malware-as-a-service business model. They develop the malware, but less-advanced gangs or individuals pay for use of that malware. In this case, it is access (or victim) as a service. GootLoader provides access to victims primarily for ransomware. The access is likely taken up by ransomware-as-a-service (RaaS) groups who sell-on the access to ransomware groups or individual criminals. For further details on this business model, see Cyber Insights 2023: Criminal Gangs.
GootLoader continues to evolve. Researchers at Cybereason have published a deep dive into the latest version.
The infection journey starts within compromised WordPress sites. These sites are given greater validity through SEO poisoning techniques, with key words likely hidden within html code on valid pages. Google Ads may also be used. With a high search engine ranking, potential victims are more likely to visit the compromised site.
The primary targets are healthcare and finance within English speaking countries, such as the US, the UK and Australia.
If a victim is drawn into a watering hole WordPress site, he is provided with a ZIP file containing a malicious JavaScript. This is described as stage-1 of the GootLoader infection. The JavaScript establishes persistence by creating and running a ‘Customer Engineering’ scheduled task. It also generates a second JavaScript file (stage-2 of the infection) which is 40 MB in size (random junk code is added, probably to confuse and evade detection).
The Customer Engineering task has been configured to execute this large new JavaScript file. It ultimately provides PowerShell code, which executes a command and control function every 20 seconds using random GootLoader C2 URLs as parameters. It uses system discovery calls to obtain the environment variables, processes, desktop items and disks on the victim machine. This data is compressed, and encoded, and sent to the C2 disguised as a cookie.
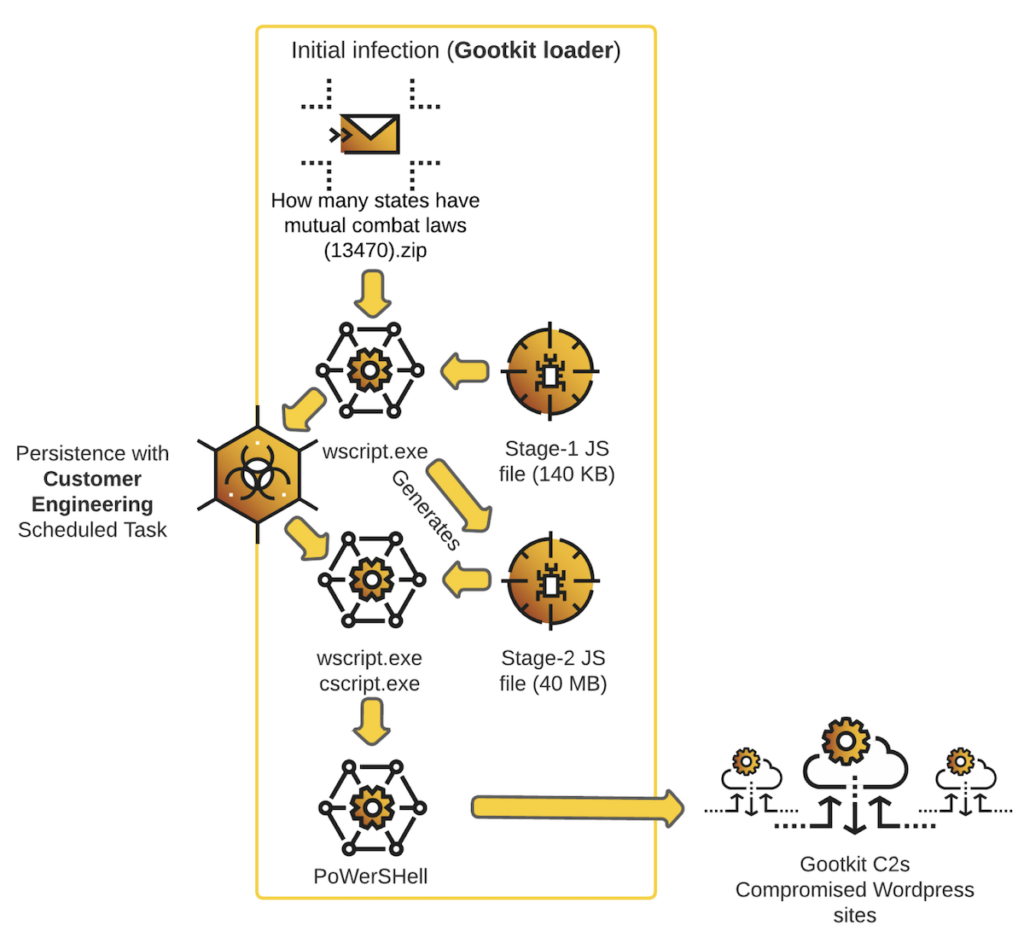
As an aside, the researchers used ChatGPT to make some of the PowerShell code more easily understood. It was used, for example, to change the original variable names into more descriptively pertinent names. This it did effectively, but researcher Loic Castel told SecurityWeek that ChatGPT’s value to seasoned researchers is limited. “It cannot help with the more complex work – couldn’t help with the de-obfuscation – but it may be used by junior researchers in more basic stages.”
Lateral movement starts with disabling Microsoft Defender, and proceeds with Cobalt Strike loaded through DLL hijacking. SystemBC is deployed.
Cybereason was unable to see the final effect of GootLoader. The instance comes from its own telemetry where it detected and stopped GootLoader’s progress. The final malware deployment didn’t happen. But they did detect the deployment of SystemBC.
“SystemBC is what we call the precursor of ransomware,” explained Castel. “We often see it hours, maybe days, before the ransomware is actually deployed. This is something that is often deployed just before a ransomware attack.”
Any subsequent ransomware attack would almost certainly not have been delivered by UNC2565. Their function within the modern criminal ecosphere is to provide access to victims, and to sell that access to other criminals. The final payload is not pre-defined, but it seems likely to be particularly relevant for ransomware.
GootLoader is not a specifically targeted attack. However, some generalized targeting is achieved through the development of the original watering hole process. This suggests that this instance of the malware is aimed at the healthcare and finance sectors within English-speaking countries.
Cybereason assesses the GootLoader threat level as ‘severe’. The malware uses a combination of evasion and living off the land techniques, and its presence is unlikely to be spotted by anything other than AI-assisted anomaly detection.
Related: Ransomware, Malware-as-a-Service Dominate Threat Landscape
Related: Recent GootLoader Campaign Targets Law, Accounting Firms
Related: Mouseover Macro Campaign Delivers Gootkit Trojan Via PowerPoint
Related: GootKit Trojan Targets Banks With Redirection Attacks
The post A Deep Dive Into the Growing GootLoader Threat appeared first on SecurityWeek.
The New York Office of the Attorney General has announced punitive measures against Patrick Hinchy and 16 of the companies he owns, for illegally promoting spyware.
Since 2011, Hinchy has owned and operated numerous companies, including the 16 investigated by the New York OAG, for selling and promoting spyware targeting Android and iOS devices, including Auto Forward, Easy Spy, DDI Utilities, Highster Mobile, PhoneSpector, Surepoint, and TurboSpy.
Once installed on victim devices, the spyware would collect and exfiltrate data such as call logs, text messages, photos, videos, emails, Chrome browser data, location, and data from messaging and social media applications, including WhatsApp, Skype, Facebook, Instagram, and Twitter.
The spyware was sold to ‘customers’ looking to spy on their spouse, colleagues, or other individuals, and was installed on the victims’ devices without their knowledge and without notifying them of the data collection and exfiltration activities.
Furthermore, in order to access certain types of information, the spyware required ‘root’ or ‘jailbreak’ access. Some of the spyware also allowed customers to remotely activate the infected device’s camera or microphone, for spying or eavesdropping purposes.
The collected data was being transmitted to servers owned by Hinchy’s companies, and users of the spyware apps could access it through a web dashboard that also allowed customers to activate device cameras, unlock the victim devices, and hide or erase the spyware from those devices.
Collected data, the New York OAG has discovered, was being transmitted in an insecure manner, which exposed it to potential cyberattacks and snooping.
The investigation conducted by authorities has revealed that Hinchy and his companies focused heavily on promoting the spyware and instructing customers on how to install the software without being caught.
Customers were also led to believe that the spyware was legal, although its use without the device owner’s consent violates multiple laws.
Furthermore, Hinchy and his companies failed to inform customers of the harm the use of the software could cause, presented customers with confusing refund and data security policies, and created bogus review websites to lure customers into purchasing the spyware.
The New York OAG fined Hinchy and his companies $410,000 in penalties and ordered them to modify the software so that it would notify device owners of the data collection activities. Furthermore, Hinchy and his companies are now required to “make accurate disclosures regarding endorsements, rooting and jailbreaking requirements, refund policies, and data security”.
Hinchy and his companies are also required to delete collected data and to block customer access to that data unless customers provide an electronic acknowledgment regarding the lawfulness of the spyware.
Related: Justices Turn Away Israeli Spyware Maker in WhatsApp Suit
Related: Google Links Exploitation Frameworks to Spanish Spyware Vendor Variston
Related: Religious Minority Persecuted in Iran Targeted With Sophisticated Android Spyware
The post New York Attorney General Fines Vendor for Illegally Promoting Spyware appeared first on SecurityWeek.
Unpatched and unprotected VMware ESXi servers around the world have been targeted over the past few days in a large-scale ransomware attack exploiting a vulnerability patched in 2021.
The attacks, dubbed ESXiArgs, are still being analyzed by the cybersecurity community, but based on the information available to date, it appears that threat actors are exploiting CVE-2021-21974, a high-severity ESXi OpenSLP heap-overflow vulnerability that VMware patched in February 2021.
“A malicious actor residing within the same network segment as ESXi who has access to port 427 may be able to trigger the heap-overflow issue in OpenSLP service resulting in remote code execution,” VMware said in its advisory at the time.
Proof-of-concept (PoC) code and technical details on CVE-2021-21974 were made public a couple of months after the patches were announced, but there do not appear to be any previous reports of the vulnerability being exploited in the wild.
In the ransomware attacks that surged over the weekend, threat actors exploited the flaw to hack ESXi servers and deploy a piece of malware that encrypts files associated with virtual machines, including files with the .vmdk, .vmx, .vmxf, .vmsd, .vmsn, .vswp, .vmss, .nvram, .vmem extensions, according to an analysis by French cloud company OVH.
The attacks seem to target vulnerable ESXi servers that are exposed to the internet on port 427.
OVH noted that the malware shuts down VM processes before initiating its encryption routine, but the function does not seem to work properly. In some cases, files are only partially encrypted, allowing victims to recover them without paying a ransom. There is no evidence of data being stolen in the attacks.
Researcher Enes Sonmez has found a way to recover some of the files encrypted by the ransomware.
The attacks were initially incorrectly attributed to ransomware named Nevada and Cheerscrypt (Emperor Dragonfly), but they were later linked to a new ransomware operation named ESXiArgs.
More than two thousand ESXi instances appear to be impacted according to Censys. Shodan shows roughly 800 compromised servers.
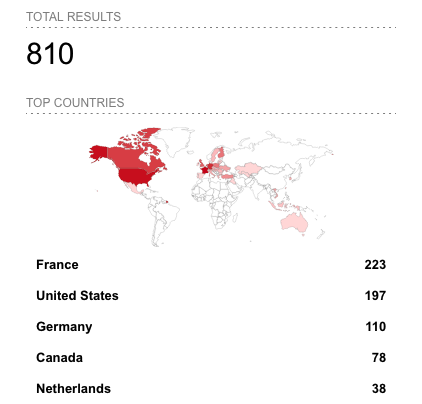
At the time of writing, many antivirus engines cannot detect the ESXiArgs malware.
Government agencies in the United States and Europe are looking into these attacks and assessing their impact.
While the malware does not appear to have file exfiltration capabilities, the ransom note dropped in the ESXiArgs attack informs victims that their data will be sold unless a payment is made. Victims are instructed to pay 2 bitcoins ($48,000) to receive the encryption key needed to recover files.
Ransomware expert Soufiane Tahiri has been keeping track of the Bitcoin wallet addresses used by the cybercriminals.
While it has become increasingly common for threat actors to target ESXi servers, the exploitation of ESXi vulnerabilities is rare.
Related: VMware Patches VM Escape Flaw Exploited at Geekpwn Event
Related: VMware Confirms Exploit Code Released for Critical vRealize Logging Vulnerabilities
The post Many VMware ESXi Servers Targeted in Ransomware Attack via Old Vulnerability appeared first on SecurityWeek.
A sophisticated piece of malware named HeadCrab has ensnared at least 1,200 Redis servers worldwide, Aqua Security reports.
Designed to run on secure networks, Redis servers do not have authentication enabled and are prone to unauthorized access if exposed to the internet.
Redis servers can be set up in clusters, which allows for data to be divided and stored on multiple servers. The structure uses a master server and slave servers for data replication and synchronization, where the Slaveof command is used to designate slave servers.
In an observed HeadCrab infection, this command was used to set victim servers as slaves to a Redis instance controlled by the attackers. Next, malicious modules from the master server were synchronized, to deploy the malware.
The malware provides attackers with full control over the infected servers and supports a series of commands that allow them to perform various actions on the victim machines.
The purpose of the campaign was to ensnare internet-exposed Redis servers into a botnet for cryptocurrency mining. Aqua identified roughly 1,200 infected servers and estimates that the attackers made an annual profit of almost $4,500 per worker, based on the identified Monero wallet.
Created as a Redis module framework, the HeadCrab malware goes undetected by some security products, according to Aqua. Upon malware execution, a module is loaded and information about the action is stored for future checks, ensuring that only one instance of HeadCrab runs.
If the module is loaded with two arguments (magic numbers), eight default Redis commands are overridden to avoid detection. The malware also deletes the Redis log file or empties it if it was recreated.
The threat also locates the dynamic loader to execute processes under its name, another way to evade detection. It also checks for several service management programs, which are later used for persistence.
Next, new Redis commands are created, allowing the attackers to control the malware. These are meant to ensure further persistence, execute commands, replace default commands with malicious ones, update magic numbers, establish encrypted communication with the command-and-control (C&C) server, reenable debugging, and restore the overridden commands.
“Our investigation has revealed that HeadCrab’s botnet has already taken control of over 1,200 servers, all infected with this malware. It is our conviction that HeadCrab will persist in using cutting-edge techniques to penetrate servers, either through exploiting misconfigurations or vulnerabilities,” Aqua Security concludes.
Related: Redigo: New Backdoor Targeting Redis Servers
Related: Many Internet-Exposed Servers Affected by Exploited Redis Vulnerability
Related: Recently Disclosed Vulnerability Exploited to Hack Hundreds of SugarCRM Servers
The post HeadCrab Botnet Ensnares 1,200 Redis Servers for Cryptomining appeared first on SecurityWeek.